Application security protects software application code and data from leaks and cyber threats. It includes all tasks that introduce a secure software development life cycle to development teams. Its ultimate purpose is to detect, repair, and ultimately, avoid security flaws in applications. It covers the entire application life cycle, including requirements analysis, design, implementation, testing, and maintenance.
Checks your software for exploitable vulnerabilities and errors. It enhances the quality of the applications while reducing costs, maximizing ROI, and saving development time.
Software applications and products have several variations in terms of features they support as well as processes they implement. Hence, application Testing ensures that a particular program or application functions properly.
The process of using hypothetical scenarios, system diagrams, and testing to secure systems and data. By identifying vulnerabilities, helping with risk assessment, and suggesting corrective action, threat modeling helps improve cybersecurity and trust in key business systems.
A manual or automated process that examines an application’s source code. The goal of this examination is to identify any existing security flaws or vulnerabilities.
This specifically looks for logic errors, examines spec implementation, and checks style guidelines, among other activities.

A service that is designed to assist your development and technical team to identify and understand the risks and threats to the application. Thereby allowing them to take remedial action against critical and non-critical vulnerabilities.


Retail

Healthcare

Insurance

Supply chain

Banking & Finance

Manufacturing
In today’s connected world, all applications are more prone to security attacks and breaches. And the sooner you can detect and resolve security concerns in the software development process, the safer your company will be.
Application security testing can prevent these attacks by uncovering application-level flaws. These tools that integrate with your development environment can make this process and workflow much easier and more efficient.

Many legacy systems that businesses use were developed before the rise of cloud computing and many other recent advancements. This leaves them in a difficult position, needing to balance the necessity of maintaining these systems with the desire to innovate, meet new customer expectations, and address new opportunities. And Application Modernization can do that and much more like:
Risk Protection
It protects sensitive data from leaks. And blocks threats from both internal and third-party sources.
Builds Trust
It will keep customers’ data secure, thus building customer confidence. Since it also protects valuable business data, it also improves trust from crucial investors and lenders.
Easier to Identify Threats
Having a consolidated and correlated view of vulnerabilities in a single platform speed up the analysis and prioritization of vulnerabilities. This leads to the identification of a vulnerability and the start of remediation in a short period of time.
Automation
Both security engineer and software developer teams will be automatically notified when something that does not comply with the agreed-upon operations occurs.




The procedure that is used to protect your application from the ever-changing attack surface without affecting its performance. Its final goal is to improve security practices and, through that, to find, fix, and prevent security issues within applications.
Different types of application security features include authentication, authorization, encryption, logging, and application security testing.
Application security controls are techniques used to enhance the security of an application at the coding level, making it less vulnerable to threats. Many of these controls deal with how the application responds to unexpected inputs that a cybercriminal might use to exploit a weakness.
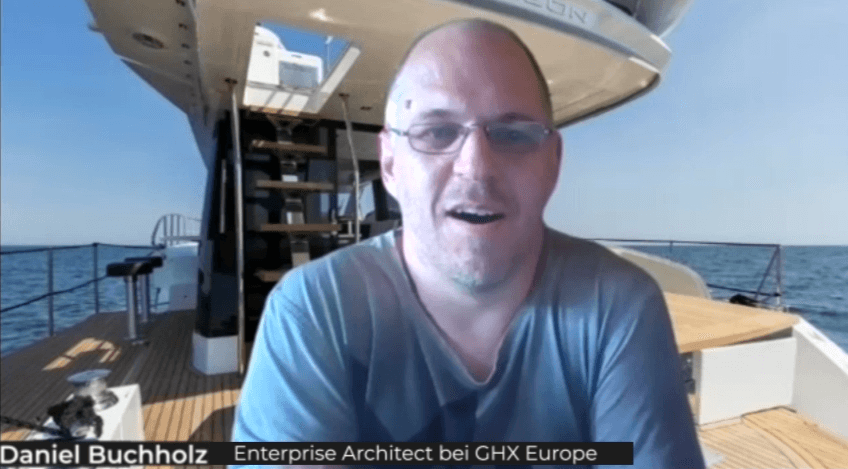
“They’re big contributors during our story grooming and design session. And they’re always very helpful and willing partners to their team members, making themselves available and really expressing a can-do attitude for getting the job done.”
Daniel Buchholz
Enterprise Architect bei, GHX Europe
CJ Singh
Chief Technology Officer, GHX
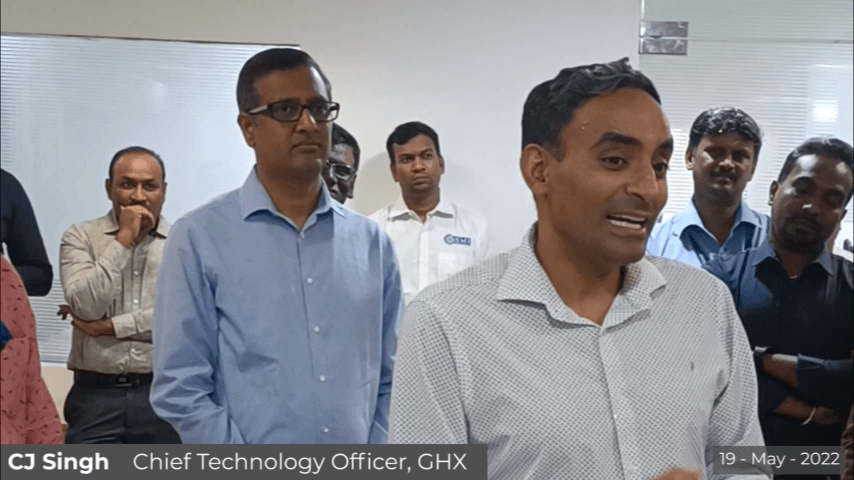
“We recently won an industrial award for this (Kiosk). It’s through an independent panel, a lot of comparisons, and all. It’s very remarkable that we won that award. So, thank you all for the effort on that.”
CJ Singh
Chief Technology Officer, GHX

“The level at which this team is operating, the rigor, the engineering practices, the process thinking through is one of the best I have ever seen.”
CJ Singh
Chief Technology Officer, GHX

“They are very humble, polite people and able to really accommodate any work pressures, any requirements. And their willingness to learn things is really great,”


“I find that I have ideas, and they are great with expanding on that and even make me see things that I wouldn’t normally see.”
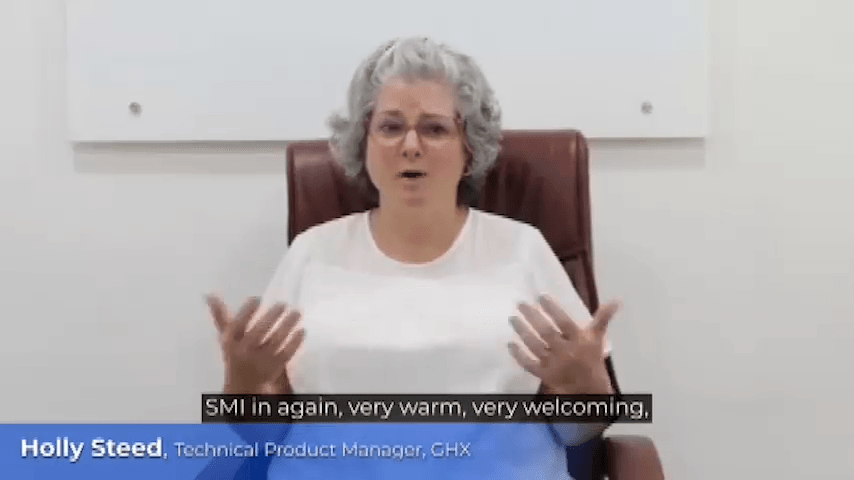

“We have come a long way. We still have a long way to go. But I want to recognize each one of you for your hard work, your attitude this whole time, and especially the flexibility and willingness to work extra hard.”


Never miss any updates. Subscribe to our newsletter to stay informed

Download Case Study